In today’s digital age, securing yourself from email phishing attacks is crucial, especially for individuals and small business owners.
This guide offers practical steps to strengthen your defenses and prevent Email phishing scams effectively.
Note: In the following, I will address only the Email phishing type; there are other forms of phishing that you can learn about from my other article: What Is Phishing, Its Different Types, and How It Works.
Part A – Identifying email phishing – A fundamental skill:
Identifying phishing emails from legitimate ones requires paying attention to specific indicators:
1. Check the writing style of the email
When assessing an email, pay attention to its writing style:
a- Alarming subject:
Phishing emails often have alarming subjects, aiming to create panic or fear. Watch out for urgent language pressuring immediate or urgent action. Legitimate entities won’t pressure you to take urgent actions.
Often, you’ll get phishing messages with subjects like “Immediate action needed” or “Security alert: Your account may be compromised.”
b- Suspicious content:
Be cautious of content:
- offering deals that seem too good to be true;
- or requesting personal information, passwords, or confidential data.
These are common tactics used by phishing attempts.
c- Language quality:
- Spelling mistakes: Legitimate companies usually proof-read their communication, while phishing emails commonly contain spelling mistakes.
- Generic tone: Beware of emails lacking personalized information. Phishers often use a one-size-fits-all approach to target a broad audience.
Scrutinize the language for inconsistencies or signs of unprofessionalism.
2. Scrutinize sender address
When inspecting the sender’s email address, be vigilant to identify potential red flags and steer clear of phishing scams. Follow these guidelines:
a. Check for inconsistencies:
Examine the displayed name and the email address for inconsistencies. If the name or nickname before the @ symbol differs significantly from the name claimed in the email content, exercise caution.
b. Verify organization alignment:
Ensure the sender’s email address aligns with the organization they claim to represent. Legitimate entities use official domains.
For instance, a phishing email sender might use a Gmail account while posing as a Microsoft or PayPal staff member, as they cannot replicate @microsoft.com or @paypal.com addresses.
c. Watch for variations and misspellings:
Be cautious of slight variations or misspellings in the domain name after the @ symbol.
For example, a phishing attempt might use “@paypa1.com” instead of “@paypal.com” to mislead recipients, or “@fedexmdfofyrj.com” instead of “@fedex.com”. See the screenshot below:
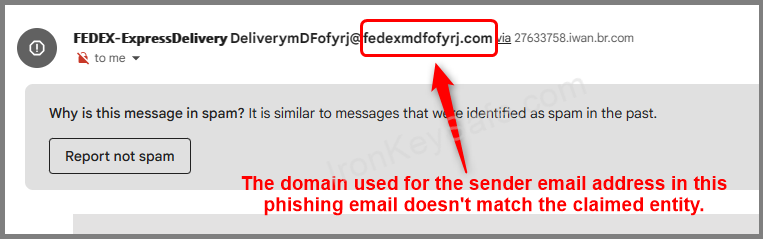
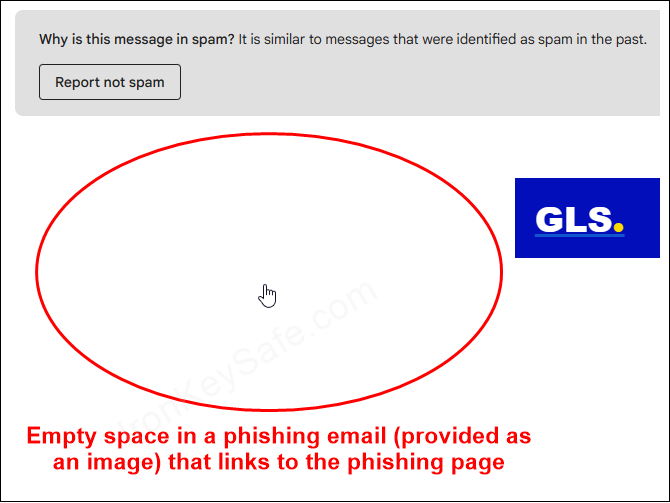
3. Do not click on empty space
Sometimes, phishers provide the email as a linked image, so even when you’re avoiding to click their buttons and want just to place the cursor into the empty space of the email, it will take you to the phishing page!
So:
- avoid clicking into the space of the phishing email;
- or keep an eye on the cursor of the mouse when hovering over this space: If the cursor turns into a hand shape, and not a regular arrow or text cursor, it indicates a linked image!
See screenshot below:
4. Hover over links
Take a moment to hover over embedded links and reveal the real URL. Verify that it aligns with the claimed destination. Exercise caution if the URL appears altered or unfamiliar.
For instance, a phishing link might masquerade as “https://yourbank-login.com,” but a hover reveals its true and suspicious destination, or as in my example illustrated below a link faking FedEx company takes to a storage.googleapis.com phishing page.

5. Verify email legitimacy
Ensure the authenticity of the email by cross-referencing it through established communication channels.
Reach out to the claimed entity directly using their official contact page, website email, or even by phone if possible.
Part B – Handling phishing links and attachments with caution:
Phishing links and attachments often serve as gateways for cyber threats. Secure your digital space with the following precautions:
6. Don’t rely on provided links
Avoid clicking on suspicious links.
Always verify URLs by directly visiting the website instead of relying on provided links.
7. Exercise caution with suspicious attachments
Avoid opening attachments from unfamiliar sources to prevent potential malware infections that could compromise your computer or network security.
Verify the legitimacy of the sender before downloading any attachments.
Lastly, and before opening them, make sure to scan them with your antivirus software.
Part C – Secure browsing:
8. Check web pages URLs and content
If you clicked on the links embedded in the suspicious email you received (despite all my warnings from the above paragraphs!):
- Examine the URL in the address bar to ensure it aligns with the official website address.
- Verify in the address bar that the website uses HTTPS (and not HTTP).
If the HTTP or HTTPS protocol used isn’t visible, just double click the in the address bar.
Keep in mind that the mere presence of HTTPS encryption isn’t enough by itself, but it signals a certain level of security.
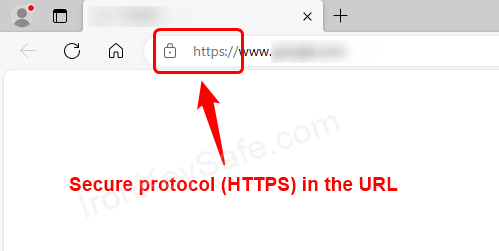
- Be wary of pop-ups asking for personal information or an unexpected prompt to download software. These can be signs of phishing pages.
Part D – Reporting phishing attempts:
Reporting phishing attempts enhances collective defense.
9. Prompt reporting of phishing attempts
The best ways to report a phishing email, from the simplest and direct one to the more advanced, are:
- Report it to your email provider: reporting to the email provider helps refine email filters, enhancing protection for you and others in the future;
- If you’re an employee, report it also to your IT department: timely reporting to IT departments enables quick action to prevent further attacks and safeguard your organization’s sensitive information;
- Report it to the Anti-Phishing Working Group (APWG).
- In the US, report it to the Federal Trade Commission (FTC).
- In the US and if you think the email is dangerous enough, report it to the Internet Crime Complaint Center (IC3).
I will detail very soon these 5 ways in a dedicated article.
After reporting the phishing email, consider also blocking the sender to prevent future emails from the same source.
Part E – Utilizing security tools and features:
Security tools and features you can use are email filters, anti-phishing tools, firewalls, antivirus, and antimalware solutions.
10. Configuring email filters
Be proactive by configuring email filters to identify and prevent phishing attempts from infiltrating your inbox. These filters carefully examine emails for phishing keywords and phrases, verify the legitimacy of the sender, and block messages showing suspicious behavior.
This proactive approach significantly reduces the risk of falling victim to email phishing scams. Implementing rules within email filters proves to be an effective strategy.
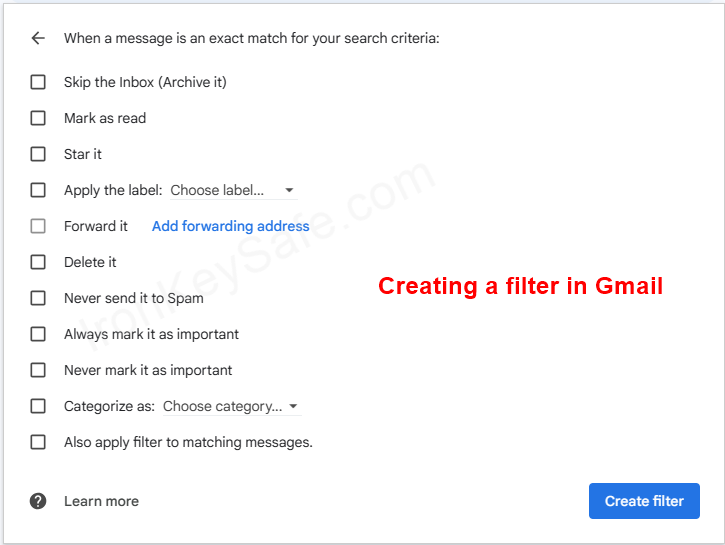
Examples of rules you can establish in your email filters of your email client software or website:
- A rule that directs emails with links or attachments to a specific folder for thorough review before opening.
- Or a rule that automatically deletes emails from a sender that is not in your contact list, or that has a suspicious domain name, such as a misspelled or unfamiliar one.
This practical approach not only declutters your inbox but also minimizes the chances of accidentally engaging with harmful links or attachments.
11. Leverage anti-phishing tools
Some reputable anti-phishing tools are:
- IRONSCALES.
- Proofpoint.
- Bitdefender.
- Microsoft Defender for Office 365.
- Cisco Secure Email Threat Defense.
- Barracuda Sentinel.
- Symantec Email Security.cloud.
- Avast.
- GreatHorn.
- Agari.
- Avanan.
- PhishTitan.
Some of the free anti-phishing solutions are:
- Avast Free Antivirus.
- Avira Free Security.
- PhishProtection.
12. Leverage firewalls solutions
Implement robust security measures with firewalls solutions. These tools actively detect and prevent suspicious activities, adding an extra layer of protection.
Consider these reputable firewalls known for their effectiveness in combatting various cybersecurity threats, including phishing:
- Fortinet FortiGate Next-Generation Firewalls NGFW.
- Cisco Firepower Next-Generation Firewall NGFW.
- Palo Alto Networks Next-Generation Firewall NGFW.
- Check Point Quantum Security Gateways.
- Sophos Firewall.
- WatchGuard Firebox.
13. Leverage antivirus and antimalware solutions
For Antivirus solutions, consider reputable options like:
- BitDefender.
- Norton.
- TotalAV.
- McAfee.
For Antimalware solutions: I found Malwarebytes Anti-Malware (MBAM) to be the best one.
14. Use Two-Factor Authentication (2FA)
Enable Two-Factor Authentication (2FA) whenever you can. This extra security layer prevents unauthorized access, even if your passwords are compromised.
2FA requires using a second method (besides your password), like a phone text message or an authentication app, to confirm your identity.
Part F – Stay updated:
15. Stay updated
Make sure to keep your security software, browsers, and email applications up to date. Regular updates guarantee you have the latest security features.
It’s also crucial to stay informed and educate yourself and your team, if applicable, about the latest phishing techniques and how to identify them. Attend training sessions, subscribe to security newsletters, and stay current with industry news.
By staying informed, you can strengthen your defense against email phishing attacks and safeguard your business’s assets and reputation.
Part G – Mobile device security:
16. Extend your security practices to mobile devices
- Apply all the above security practices to your mobile device.
- Scrutinize mobile app permissions and limit them. Only grant necessary permissions to apps, preventing potential misuse of your data.
Final thoughts on how to protect against email phishing scams
Shielding both your personal information and your business reputation from the harmful effects of email phishing attacks is crucial.
To defend against such threats, it’s essential to implement the practices outlined above. By embracing these best practices, you can lower the risk of falling victim to email phishing attacks and protect both your personal and business-sensitive data.
Brian is a dedicated professional in IT security since 2010. With a strong commitment to enhancing cybersecurity practices, he shares in this website valuable insights to empower individuals and businesses in securely navigating the digital world.

Actually no matter if someone doesn’t understand
afterward its up to other viewers that they will help, so here it occurs.